By:
Oliver Rochford, Security Evangelist, Securonix
Stephen Moon, Data Platform Architect, Snowflake
The U.S. Office of Management and Budget (OMB) published a memorandum on August 27, 2021 titled “Improving the Federal Government’s Investigative and Remediation Capabilities Related to Cybersecurity Incidents.” The memo details security event management requirements for federal agencies, and it expands upon Executive Order 14028, “Improving the Nation’s Cybersecurity,” which the White House published on May 12, 2021 in response to the Colonial Pipeline and SolarWinds breaches.
To guide implementation, the memo outlines a maturity model with requirements across four tiers, Event Logging (EL) EL0 to EL3, with each tier expanding the scope of event collection and monitoring. The OMB envisions an aggressive timeline over two years for agencies to comply, and federal agencies are already expected to have a basic EL program up and running in 12 months, by August 27, 2022.
The ultimate objective is to collect, aggregate, and analyze all relevant event data and make it available to the highest-level security operations center (SOC) and the heads of each agency.
The first milestone on October 26, 2022, which is for federal agencies to assess their maturity against the new Maturity Model for Event Log Management, is rapidly approaching. Federal agency CISOs should be cautious. Most agency security teams will be busy planning how to meet the ambitious deadlines. Considering the aggressive timeline the OMB has laid out, they cannot afford to make mistakes or experiment.
Many of the technical requirements are based on common best practices, for example, from NIST, and are standard for any modern enterprise SIEM solution. They include considerations such as centralized and role-based access, event and log data integrity, and standardized log schemas.
Other requirements, however, go beyond what a traditional SIEM solution can deliver, mandating additional technologies such as Security Orchestration, Automation, and Response (SOAR) and User and Entity Behavior Analytics (UEBA).
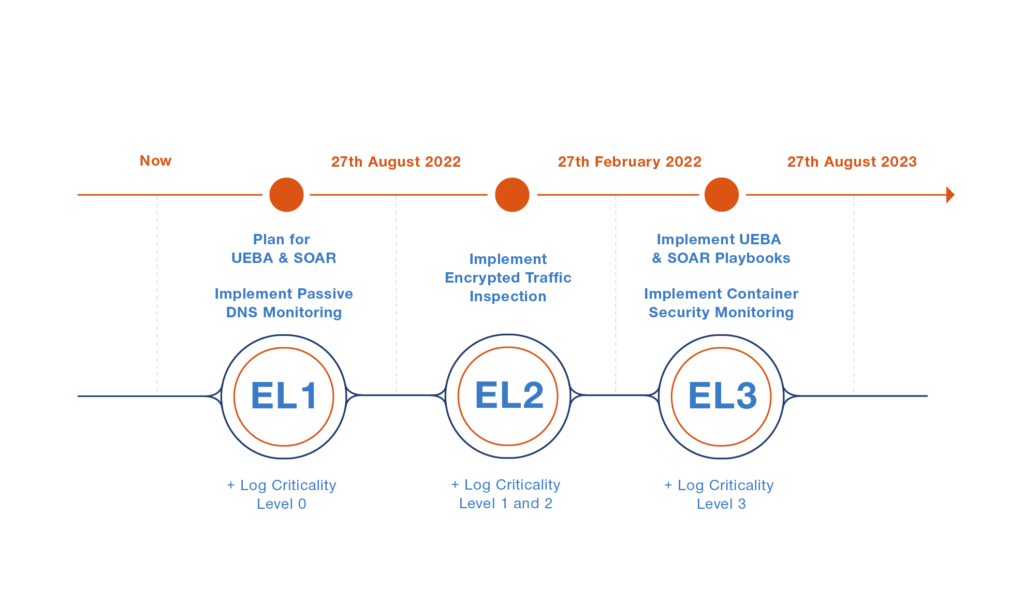
Figure 1: Maturity model for EL implementation timeline
Massive event collection scope and retention periods will limit and define federal agencies’ choices
A full 32 of the memo’s 44 pages are taken up by an extensive appendix (P13, “Appendix C: Logging Requirements – Technical Details”) detailing the log categories to be collected, including the associated event data and retention times, by criticality level.
The list is extensive and, as the table below shows, comprehensive, and it goes beyond what most security teams usually collect for security monitoring purposes.
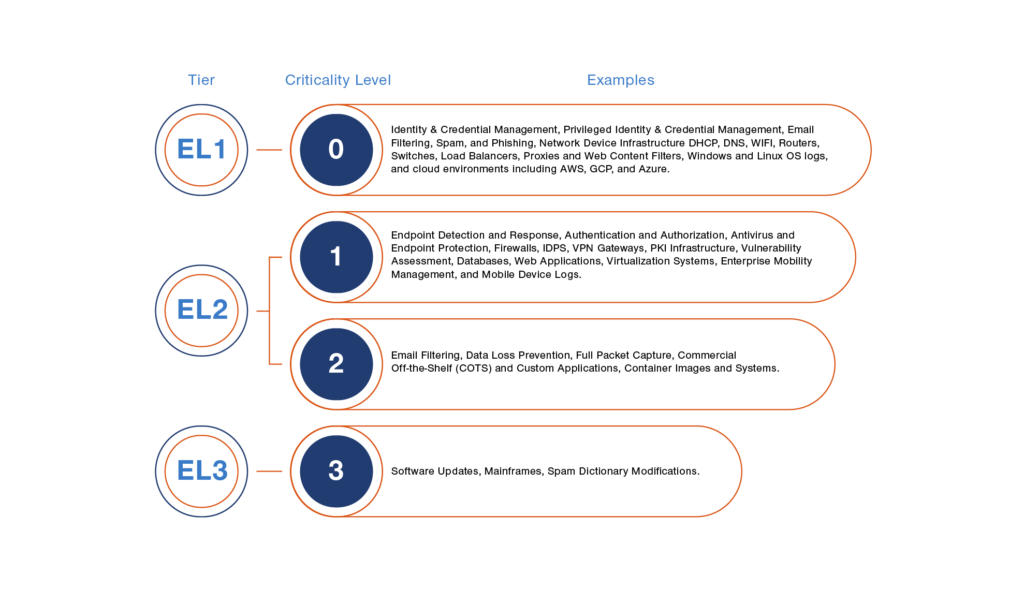
Figure 2: Sample list of event data sources to be collected and stored
Many SIEM solutions do not support all of the listed data sources with out-of-the-box content such as connectors, collectors, parsers, and correlation rules.
It is possible to manually add a few unsupported event logs, but this quickly becomes time- and labor-intensive and requires ongoing maintenance, so it doesn’t scale. When data sources are manually added, care must also be taken to fulfill the requirements for event forwarding and protecting and validating log information, as described in “Appendix A: Implementation and Centralized Access Requirements.”
The stipulated retention time frames also exceed what many typical SIEM and log management solutions, especially those deployed on premises, can deliver. When multiplied by the number of different events and logs to be collected, the amount of data to be stored for 30 months is huge.
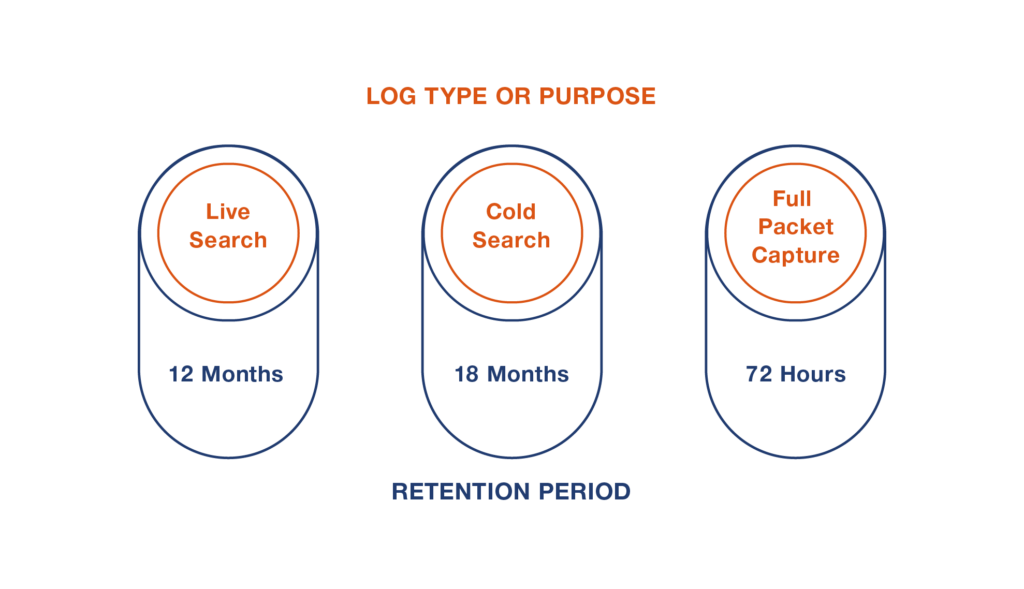
Figure 3: Data retention requirements
Finding a technical architecture that is operationally effective at this scale while still being affordable is a challenge. To save money, agencies could try to use some large-scale operations support system (OSS) data architectures such as Hadoop or Elastic, and run this in a cloud service such as Amazon Elastic Container Service (Amazon ECS) for scalability.
Of course, the downside to such an approach is that using a generic data solution means having to develop security content such as detections, queries, dashboards, and playbooks from scratch, requiring many man-hours and in-depth knowledge and expertise across diverse threat and security scenarios.
What is clear is that a traditional SIEM solution is not the right solution here. What is needed is a security data platform.
Legacy SIEM solutions won’t do: Agencies need integrated SIEM, UEBA, and SOAR
The memo may, at first glance, look like it’s all about security information and event management, but it is actually much more than that. Because, beginning with the milestone to achieve EL1 on August 27, 2022, federal agencies must also plan to deploy user behavior analytics (UBA) and SOAR capabilities. Usually this would entail two or even three different technologies—unless a solution that combines all three, such as Securonix, is used.
Agencies have 12 months to plan and implement a UBA program suited to their needs, monitoring, at a minimum, all user and non-user accounts for the following scenarios:
- Compromised user credentials
- Privileged-user compromise
- Improper asset access
- Compromised system/host/device
- Lateral movement of threat actor
Initially, the list does not really seem that large, but the use cases are actually use categories and can comprise a considerable set of additional subrequirements. For example, detecting the lateral movement of a threat actor requires comprehensive visibility into network traffic, with all that entails.
The memo also specifically calls out machine learning and artificial intelligence, so agencies must evaluate whether their existing SIEM solution has advanced native UBA or offers an upgrade path or third-party integration to meet this need. Off-the-shelf generic database or data lake technologies may offer machine learning add-ons, but agencies leveraging these will have to research, develop, and maintain an extensive set of threat models themselves.
Following the same timeline as for UBA, federal security teams must also plan and implement SOAR playbooks to automate incident response and threat-hunting tasks. How widely playbooks should be applied to the whole range of collected event sources is left unclear. Most SOAR solutions provide customizable playbooks for a range of use cases and scenarios but will still require extensive customization to tailor them for use with different events and third-party technologies. Agencies should not underestimate the amount of effort, and especially time, this may involve.
Agencies must also ensure that whatever architecture they chose for event collection, storage, and search is also compatible with their preferred UEBA and SOAR solutions. The three components must interoperate seamlessly. Ideally, agencies will have a platform that integrates SIEM, UEBA, and SOAR.
Extending the detection stack for full-spectrum visibility
In addition to implicitly citing additional requirements for technologies such as endpoint detection and response (EDR), the memo also explicitly cites additional requirements for:
- Passive DNS logging
- Encrypted traffic inspection
- Container security monitoring
These additional security monitoring use cases make a lot of practical sense but are also not universally supported by many security monitoring technologies, and so they should be included in request for proposals (RFPs) and in any proof-of-concept process during solution selection.
Agencies planning for EL3 maturity should keep in mind that these technologies may require their own infrastructure and implementation projects and will also require developing supporting content and utilities in the SIEM or log management solution, including detections, correlation rules, and dashboards. Agencies should also endeavor to select a technology provider that simplifies adding these requirements, either through technology partnerships or, preferably, through a native solution.
Federal SOCs enabled by Securonix and Snowflake
Given the short timelines and the breadth and depth of requirements set forth in the OMB memo to reach EL3 maturity, federal agencies are left with few viable options. Choosing the wrong option will result in the acquisition of technical debt that likely cannot be retired in the time frame required to achieve compliance. Adding to this challenge is the fact that there are few, if any, COTS solutions that can achieve compliance with the OMB memo.
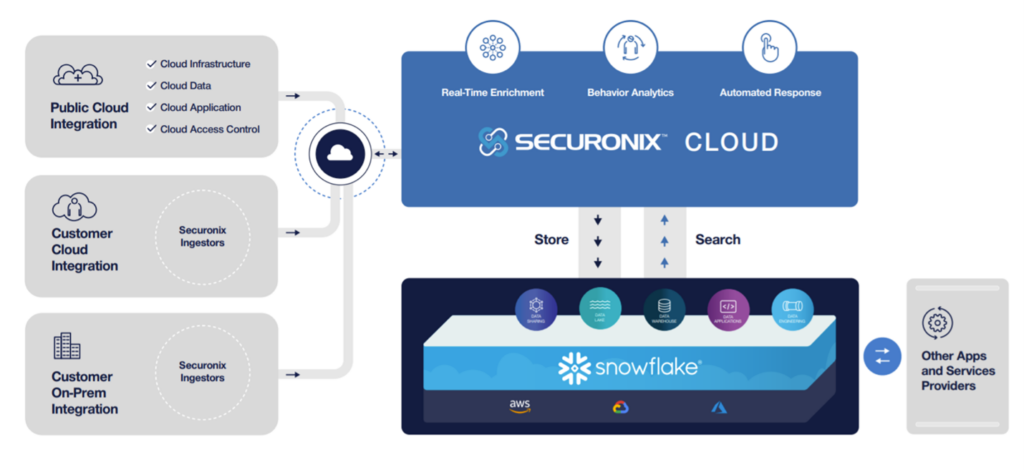
The good news is that Securonix and Snowflake have developed such a solution: Securonix Bring Your Own Snowflake . It combines next generation SIEM, UEBA, and SOAR capabilities with a secure data platform. This solution allows customers to leverage a connected apps model in which Securonix connects directly with a Snowflake customer’s account—allowing customers to manage their security data in their own Snowflake security data lake. Federal agencies can then leverage Snowflake’s near unlimited ability to securely store and process any volume, velocity, and variety of data at scale—accessible through Securonix Next-Gen SIEM for security visibility, analytics, and intelligence-based incident response.
Unlike traditional SIEM solutions that use a data consumption model, this hybrid approach enables data, services, and applications to be optimally deployed between the security data lake running in Snowflake and Securonix’s cloud-native infrastructure. Compute power is virtually unlimited and can be scaled as needed for rapid investigations of up to petabytes of data. Snowflake’s consumption-based pricing means that customers only pay for the resources they use, which allows customers to operate a highly cost optimized solution. And, best of all, the solution is delivered from a FedRAMP-authorized environment.
By employing their own Snowflake deployment for their security data lake, customers can take advantage of Snowflake’s industry leading, and often unique, capabilities concerning their security data. First, because Snowflake’s platform is supported on all three major cloud service providers (CSPs), customers will have the same experience regardless of whether they are in one CSP or all three CSPs. Second, Snowflake Secure Data Sharing capabilities will allow federal customers to securely share security data within their agency or with other federal agencies without moving the data and, thus, negating the technical and monetary risk and cost of implementing complex data pipelines. Because Secure Data Sharing does not require data movement, it allows the data owner to maintain complete control over and visibility into who has access to the data, and access can be revoked by the data owner at any time. Secure Data Sharing will also allow federal agencies to seamlessly deploy other services and tools against their security data. In addition, in conjunction with Secure Data Sharing, the Snowflake data lake solution offers a data clean room, which allows federal agencies to analyze securely shared data without revealing sensitive information such as PII.
With the Securonix/Snowflake solution, federal agencies will not only meet the OMB deadline but will also build a future-proof and sustainable security program with many additional benefits, including:
- Single source of facts: All logs, assets, and configurations can be analyzed together, removing silos and reducing complexity.
- Transparent pricing and cost optimization: Store near-unlimited amounts of data at affordable cloud rates and pay Snowflake only for the compute resources used.
- Faster detection and response to threats: The Centralized Securonix Next-Gen SIEM solution streamlines investigation and acts as an extension of the customer’s security data lake in Snowflake.
- Simplified data security and governance: Having a single security model and set of data enables consistent implementation of security and privacy controls for data protection.
- Cloud platform agnostic: Retain data in the cloud platform of choice without compromising threat detection and response capabilities.
The Snowflake Connected Apps model leveraged by Securonix delivers a set of advantages and benefits that enable organizations to meet the OMB requirements on time.