Abstract:
Password vulnerabilities are a critical issue. Today, with several online accounts (business, personal, social) to manage, people struggle with password management. An increasing number of online shoppers, employees, and even IT experts face security breaches due to password-related vulnerabilities. It is critical to understand the current password practices of people. This research, “Top Password Strength and Vulnerabilities: Threats, Preventive Measures, and Recoveries,” is an attempt by GoodFirms to understand the top threats, preventive measures, and best practices in password management. An online survey was carried out between 16th October 2021 and 22nd October 2021. A total of 210 responses were collected. The survey queried selected participants (IT experts, Employees, Cybersecurity personnel) across the world on their password management practices and techniques. The research further analyzes the best practices for password management and the utility of tools such as a password manager for effective password management.
Table of Contents:
Introduction
Types of Password Vulnerabilities
Password vulnerabilities created due to User Unawareness and Errors
Password Vulnerabilities Created Due to Poor Organizational Infrastructure and Policies
Survey and Data Analysis:
- 62.9% People Change Password Only When Prompted
- 45.7% People Reuse a Password For Multiple Sites/Applications
- 52.9% People Share their Password With Colleagues, Friends, Family Members
- 67.1% of the People Believe that Managing Passwords For Multiple Accounts Is Not A Waste of Time
- 35.7% of the People Still Jot Down Their Passwords On Paper, Sticky Notes, or Use Planners.
- 30% of the Users Have Experienced Security Breaches Due to Weak Passwords.
- 88.6% of the Surveyees Use Two-Factor Authentication
- 57.1% of the Respondents Say they Use 'Show Password' Option Only Sometimes
Best Password Practices in 2021(Experts’ Views)
How to Strengthen RDP (Remote Desktop Protocol) Access and Protect its Password Credentials?
The Future of Password Security
Key Findings
Conclusion
Introduction
Password security is a pressing concern for businesses of all verticals. Whether it is through brute force, misconfiguration, pretexting, ransomware, backdoor release, privilege abuse, or other hacking methods, password stealing is a nuisance that organizations, employees, and even cybersecurity experts deal with every day. Password breaches and sophisticated brute attacks, and unauthorized attempts to steal passwords by infecting systems with malicious entities have skyrocketed in recent times. While passwords can protect the data to a certain extent, complete security of data and confidential information still rests on how well the passwords are managed. In most cases, password vulnerabilities stem from not following the best password practices suggested by cybersecurity experts.
This survey from GoodFirms entitled- “Top Password Strengths and Vulnerabilities: Threats, Preventive Measures, and Recoveries,” attempts to understand the current password behavior of online users and intends to uncover the best preventive measures to protect and secure passwords from attacks or breaches.
Types of Password Vulnerabilities
Password vulnerabilities refer to elements that make passwords weak, unsafe, and easier to be stolen. From password management flaws due to user-made errors to poor IT infrastructure and unsecured networks used by organizations, there are a plethora of reasons that make a password vulnerable.
Password vulnerabilities Created Due to User Unawareness and Errors
These vulnerabilities are created when users fail to safeguard their accounts due to poor awareness, and errors in creating passwords. The errors stem from many reasons. The National Institute of Standards and Technology's (NIST) Digital Identity Guidelines indicates “length and complexity requirements” can “significantly increase the difficulty of memorized secrets," and "can increase user frustration…" Users can look for a counterproductive way - to use easy passwords! Often they fall victim to hacker activities and end up losing their password credentials.
Few Prominent Vulnerabilities Include:
Phishing: Phishing is an attack where hackers trick users to click a similar-looking website set up by them to steal credentials. For instance, a user gets an email to reset the password mentioning that the account credentials have been compromised, and therefore a password reset is required. The link is sent in the email. The link takes users to a similar-looking page that they generally visit. They are tricked into entering their current password and user ID. The user loses credentials as they enter a password on an untrusted source.
Spear Attack: Hackers target users with emails that appear to be from acquaintances with messages such as invitations for the event or checking the invoice or providing a recommendation etc. When such content attachments get clicked, hackers receive access to email account credentials.
Whaling: In whaling attacks, hackers send an email to users, which appears to be from their seniors/supervisors/managers, etc. asking for some information along with a document that is sent as an attachment. Naive users fall into this trap easily as they try to comply with their seniors’ instructions.
Smishing: In Smishing attacks, users receive SMS or email that informs them that their account is frozen and can be unfrozen only by clicking on the link provided in the SMS or email. When users click on the link, it directs the user to input their login credentials as a part of the process to unfreeze the account. As the users proceed, the password credentials are stolen.
Brute-Force Attack: Also known as trial and error hacking or exhaustive hacking, brute-force attacks use predetermined values to target an account multiple times. Modern computers can keep repeating the brute-force multiple times with different passwords, generally the dictionary ones, until the right password is cracked. Users that keep dictionary words as passwords succumb to this attack easily. Brute force won’t work when administrators block the account after a predefined wrong password input limit is crossed.
Password Spraying: It is a type of brute-force attack wherein attackers use the same password to brute-force multiple user accounts. For instance, a default password such as joseph@123 is brute-forced on multiple users that have their names starting with Joseph. The attackers assume that out of thousands of accounts, anyone who has kept a password joseph@123 can be hacked. Most account administrators don’t allow multiple password attempts on a single account. They block the account after multiple password attempts. Therefore, attackers use the same password for multiple accounts to avoid lockout. This way, the attackers attempt only one password on a single account. Users who keep simple passwords are easy victims of password spraying.
Man-in the Middle: This type of attack occurs when hackers intercept communication or information transmission between two parties that are happening over an unsecured network or system. Sharing passwords or signing in over an unsecured network put users at this risk.
Password Vulnerabilities Created Due to Poor Organizational Infrastructure and Policies
Unsecured Networks: Organizations that fail to keep their network secure by adopting the best Virtual Private Network (VPNs) policies and practices may end up losing their system passwords to hacking attempts.
Untrained Employees: Handing over password-based login credentials to employees without proper training in password practices is another reason for password hacks.
Compromised Applications and Systems: Bugs in operating systems, pending system patches, and the use of third-party applications with poor cybersecurity protocols result in password compromises.
Survey and Data Analysis:
GoodFirms surveyed 210 IT experts, employees, and heads of organizations to shed some light on the current password practices of users, repercussions of those password practices, best password practices to ensure maximum security, and experts’ take on password management tools and techniques. Below is the analysis of the results obtained in the survey.
Existing Password Practices of Survey Participants:
62.9% People Change Passwords Only When Prompted
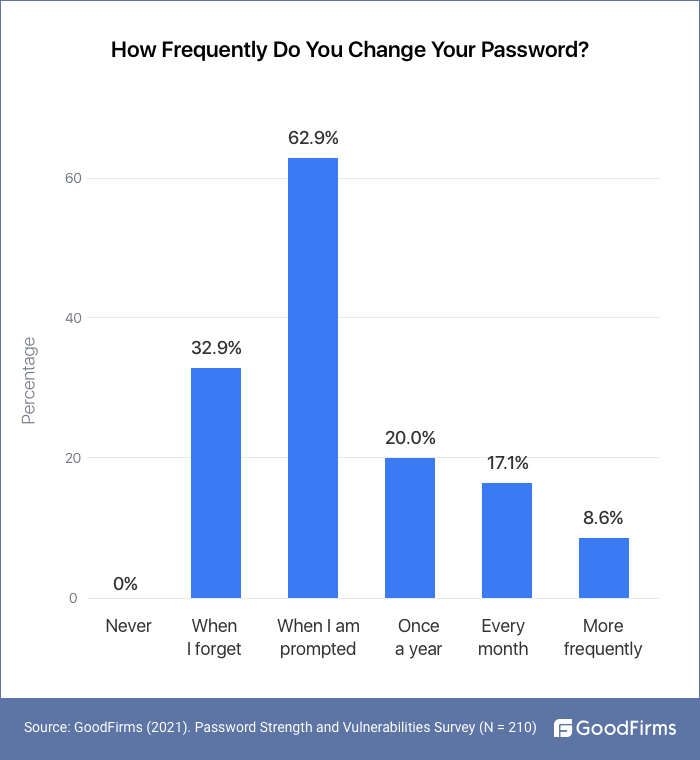
Most organizations, business applications, online platforms, etc., recognize the importance of establishing a strict password policy that requires users to change their passwords regularly. Thus, they set a password policy wherein the computer prompts the user for a new password when he/she logs on once the designated time has expired. Most software systems come with automated password expiry after a certain time period. It alerts the users of a password change requirement.
Among the surveyed respondents, a whopping 62.9 percent change their passwords only upon receiving password reset emails/ messages.
It means that rather than being proactive to change their passwords, more people depend upon alerts and mandatory password change prompts to keep their accounts secure.
Multiple research (1),(2)conducted across the world also yielded similar results, revealing that most password users are unaware of effective password policies. This, in turn, leaves people vulnerable to the attacks of cybercriminals and hackers.
Why do most people change passwords only when prompted?
- People don’t have time to monitor several applications that they have in their workstations, personal computer systems, mobile phones, etc. Therefore, mostly they change passwords only when prompted or compelled to do so by rendering them unable to log in to the account unless the password is changed.
- Also, many don’t change passwords because they forget the applications that they rarely use. Therefore, they don’t even remember that their passwords need a reset.
45.7% People Reuse a Password For Multiple Sites/Applications
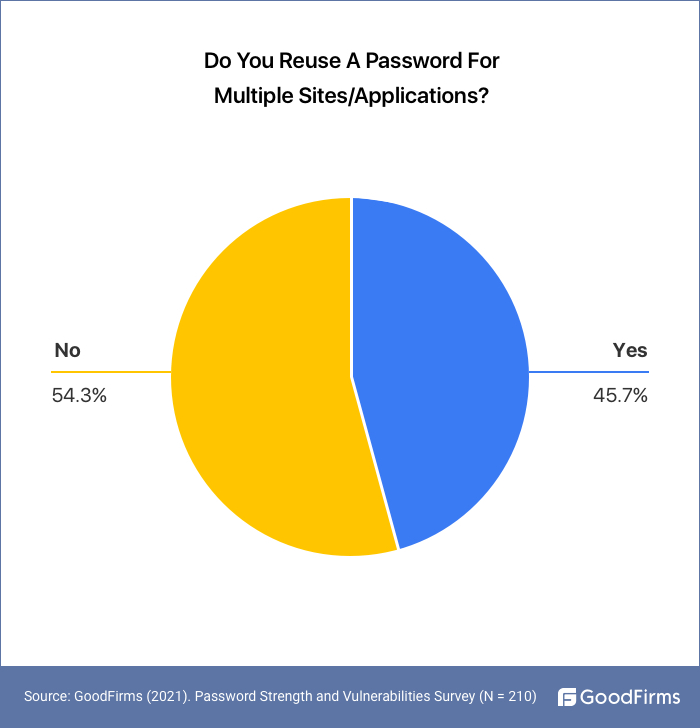
As high-value accounts such as bank accounts, financial accounts, premium accounts for online services, business apps, etc., come with enhanced security features, getting access to their password vaults is not easy for cybercriminals. Therefore, hackers exploit another loophole associated with password practices of people. Banking on the fact that more users log in to multiple sites with the same password, cybercriminals hack sites with low-security measures to get access to the login credentials of users. This information is then used to hack accounts of popular sites and payment accounts of people.
GoodFirms research found out that 45.7% of people use the same passwords for multiple sites/accounts. Password reuse is a rampant practice. When one password gets compromised, it opens a backdoor for hacking all other accounts associated with it.
Why do people use the same password for multiple accounts?
- It is easier to remember and convenient for them.
- Using the same password for multiple sites spares people from maintaining password records in written form, sheets, password managers, etc.
- Many websites, business apps, and even news apps ask people to log in to use their services; as people don't have time to create and remember multiple passwords for so many applications, they put the same password again and again.
Whatever the reasons are for using the same password across multiple sites/accounts, it is not a good practice. "If you reuse the same password, those criminals are bound to unlock additional accounts, even if those sites were never breached," says David Endler, member of Forbes Technological Council.(3)
52.9% People Share their Password With Colleagues, Friends, Family Members
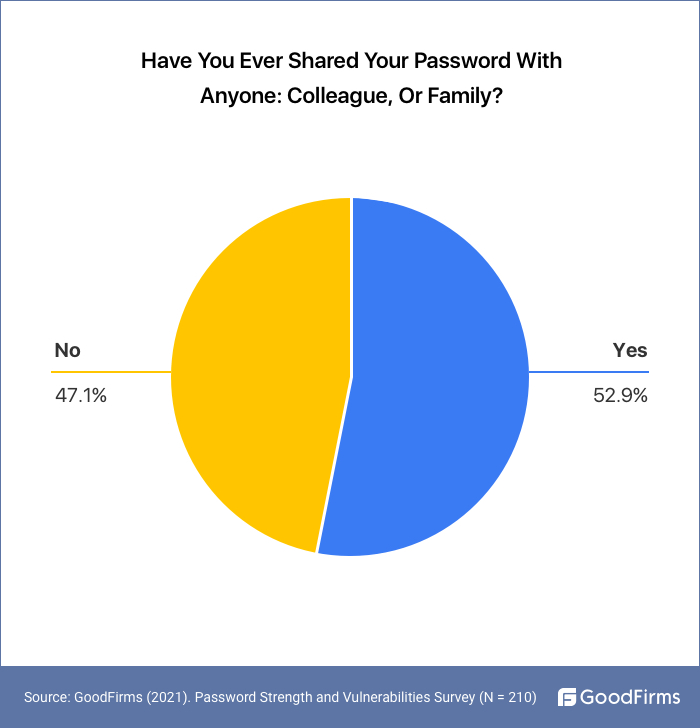
Even though advised against doing so by many cybersecurity experts, people have a tendency to share passwords with their colleagues, friends, and close family members. Even when many know that it is a risky password behavior, still people cannot help sharing passwords for multiple reasons. Most cases of privileged credentials misuse come from sharing passwords of sensitive apps with colleagues.
Our research revealed that 52.9% of respondents had shared their passwords with colleagues, friends, family members, etc., at least once in their lifetime.
Why Do People Share their Passwords with Others?
- Some people share passwords with friends and family members to enjoy more benefits from a subscription plan. For example, people generally share passwords of Netflix, Amazon Prime membership, joint accounts, wifi-password, utility apps, etc., to provide subscription benefits to their known ones without incurring additional costs.
- The password sharing practice also helps teams to access and work together on business apps.
While sharing passwords may be practical and cost-effective in organizations that allow employees to log in to office workstations only, it can be disastrous in hybrid work environments or work from a home setup where employees may use unsecured networks and personal devices. While sharing passwords is definitely a terrible idea, sharing via online chat tools, emails, or messengers is riskier. Sharing passwords online is prone to phishing attempts, malware attacks.
Sharing passwords for business accounts or financial accounts with colleagues or friends can put people in trouble if unauthorized access causes any damage to the accounts. For example, in the case of data loss, unauthorized financial transactions, or damage to system resources, the one who shared the password is held responsible. The US Computer Fraud and Abuse Act (CFFA)(4) deems sharing passwords as a violation of their guidelines and also a breach of an act in case of sharing passwords of services such as Netflix.(5)
67.1% of the People Believe that Managing Passwords For Multiple Accounts Is Not A Waste of Time
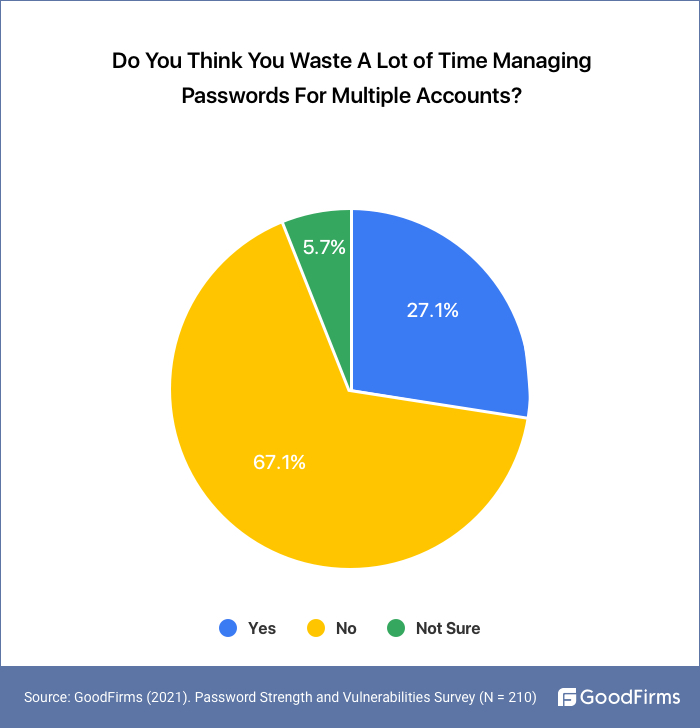
67.1% of the users feel that managing multiple passwords is not a waste of time. Digging deeper into this issue, we could find some of the patterns behind the above preferences. Users with no difficulty in managing passwords (67%) may be attributed to the fact that these users are proactive, aware, and understand the importance of managing passwords.
- They are tech-savvy people.
- Use password management tools.
- Employ alternatives to remember, organize and save passwords efficiently
- Eliminate redundant apps, rarely used accounts, and unwanted apps to keep password requirements to optimal levels
- Understand and follow the best practices for password management
- Know how to separately manage passwords for personal and professional use
27.1% Of Users Reported Wasting A Lot Of Time In Managing Passwords:
Users with insufficient knowledge of password management techniques and tools may find it difficult to manage their passwords and may end up wasting their valuable time managing passwords for multiple accounts. At the same time, 5.7% of the employees are unsure about which of the above clans to support.
35.7% of the People Still Jot Down Their Passwords On Paper, Sticky Notes, or Use Planners.
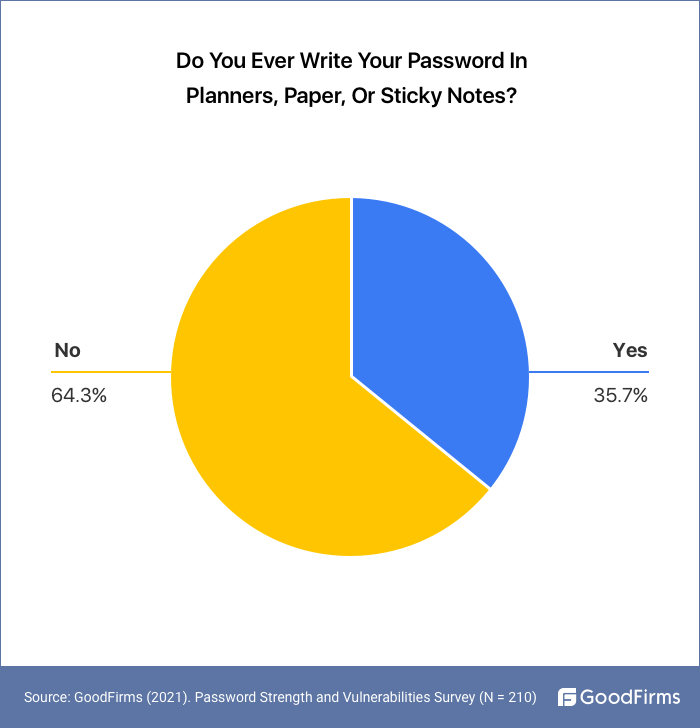
Traditionally, people used to jot down phone numbers and other essential information on a piece of paper or in their diaries. With time, these measures evolved, and added sticky notes and notepad application software, planners, etc. 35.7% of the people, according to our survey, use planners, papers, and sticky notes to write down their passwords. This is an unsafe and outdated practice.
Many employees use sticky notes for jotting down their passwords and attaching them to their workstations. It helps others in the office to easily access their workstations during their absence/leave period. While it is done intentionally to keep the workflows interrupted, any misuse may result in an extreme loss for the organization and also may put the liability on the employee who has shared the password.
Also, passwords written on papers, planners, and sticky notes can be easily stolen by unauthorized people. The paper or sticky notes are also prone to be misplaced and result in either losing or leakage of the password. In 2018, Hawaii Emergency Management Agency became a news highlight because one of its employees showed up in a public photo with his password on the desk.(6)
What could be a better option?
GoodFirms queried IT cybersecurity experts, and they suggested that using a password manager, also known as a password management system or PMS, is a better option in comparison to the traditional pen-paper methods. Password Management System (PMS) is the means to assist and maintain password policies for both individuals and enterprises. It reduces the user's burden of remembering multiple passwords and elevates the security standards to a great extent. USBs can also store numerous passwords and act as a backup to reset if the user forgets it.
A password manager can reduce the cognitive burden of remembering passwords as well as eliminate risks associated with writing passwords down on papers, sticky notes, or excel sheets.
Usability: Password managers' main use is to set up users' authentication credentials for a large number of sites—password managers can autofill(7) passwords for users on multiple sites that allow the autofill option.
Safety: 70% of experts queried by GoodFirms consider password managers as safe to use. Password managers come with high-end encryption, security, and multi-factor authentication features. Still, issues such as unencrypted metadata, insecure defaults,(8) employee misuse, etc., need to be addressed for obtaining complete safety with these tools.
Price: Most online password managers are free to use. However, some premium password managers that come with increased security, cloud protection, backup solutions, etc., charge users depending on the features and the plan.
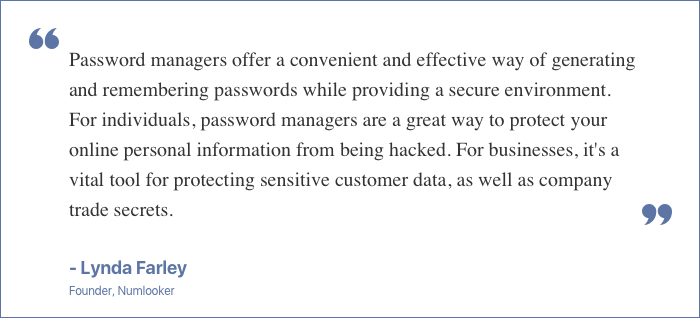
Password Managers Are a Great Solution For People With Less Cybersecurity Knowledge.
While the debate on password managers may seem never-ending, Mohamed Sehwail, CEO of FullSession.io, has a positive approach towards the use of password managers.
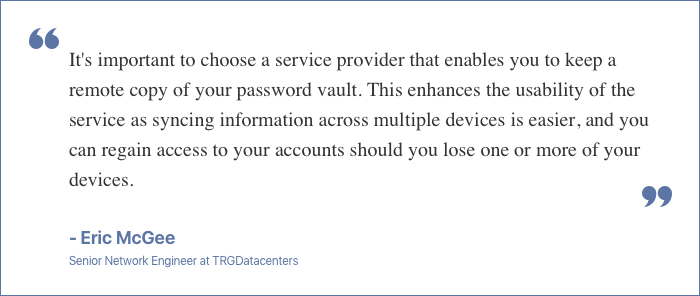
When an organization or an individual is searching for a password management tool, it is important to keep in mind that there is no one-size-fits-all approach here. The choice of tool will vary largely on the basis of its usage. For organizations or individuals that are looking for some guidance on a password management tool, Eric McGee offers expert advice.
Now, many leading brands, companies, online websites, etc., are creating consumer-facing applications that come with inbuilt-password managers and password generating tools to simplify and expedite password recalling for consumers.(9) Password managers make more sense for organizations where the IT department has to manage thousands of passwords and employee login credentials. Without PMS, the process can become cumbersome, ineffective, and impractical. PMS is an easy way to recover passwords even if it is hacked.
30% of the Users Have Experienced Security Breaches Due to Weak Passwords.
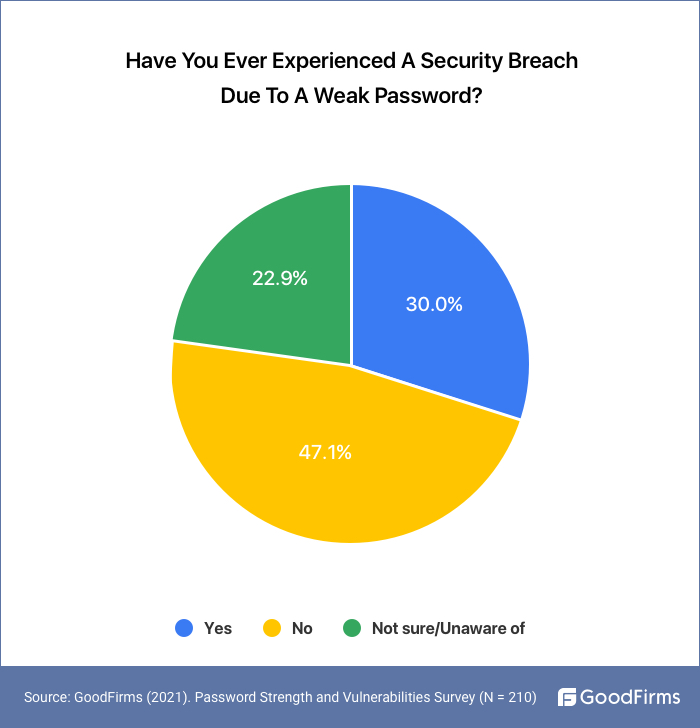
Security breaches are threats that crash individuals or SMEs and even big-wig companies like Facebook, US Cellular, Pixlr, and Memecast. The year 2021 is the worst so far in terms of security breaches.(10) The security breaches may result in loss of data, money, repute, sensitive information, and credentials. 30% of respondents in our survey reported a security breach due to weak passwords. Weak passwords are the category of passwords that are easy to guess and decrypt like the most commonly used passwords. NordPass released its list of the most commonly used weak passwords for the year 2021. These passwords can be cracked within a second. In the same report, NordPass also lists down the most vulnerable and high-risk countries according to password leak rate per capita. The USA, Russia, Canada, Australia, Poland, France, Germany, Italy, Denmark, Belgium, Ireland, Greece, and Slovakia, are indicated as the most affected regions of password leaks in 2021.
Usually, the combination of a User ID and password is enough to avoid hacking. But it is also true that passwords can give a false sense of security. The hackers are aware of this and attempt to crack the passwords as a way of gaining access to the computer systems. A problem with relying only on passwords is that more than one person can know a password. More often, it is not intentional. There is also no way to know who, apart from the password owner, is aware of it. Due to this, it is not enough to rely on just passwords for information security. People can turn on 2-factor authentication or multi-factor authentication to make their accounts safer.
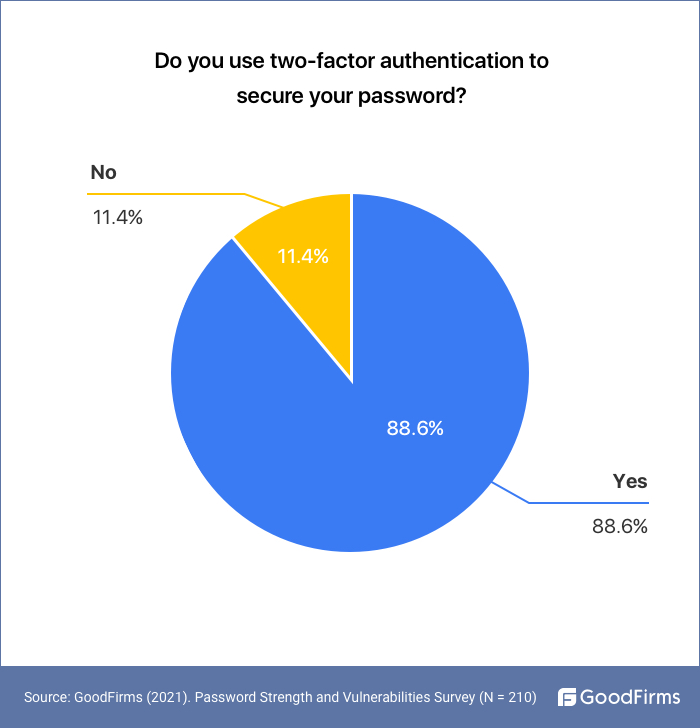
88.6% of the Surveyees Use Two-Factor Authentication
With the growing online transactions, frauds and cyber risks are increasing too. Therefore, it becomes mandatory for the users to employ double-layered or two-factor authentication. Hacking techniques are updated, and if the pattern is simple, intruders can use dictionary attacks on user-generated passwords. 20% of the passwords consist of just 5000 patterns.(11)
How Two-factor Authentication Adds a Double-Layer of Protection?
Our survey found out that the maximum number of people (88.6%) are aware of and practice two-factor authentication. 2-FA came into existence as an alternative method to strengthen the security of user data. 2-Factor Authentications further break into three types and require the use of at least two of the below to complete:(12)
- Information: It is the data known to the user (password)
- Ownership: It stands for the security token owned by the user (hardware device like a mobile phone)
- Inherence: It symbolizes the user itself, say biometric traits.
Specific traits make two-factor authentication appropriate for security purposes.(13) It includes trustworthiness, impact, adoption, and usability. Many financial institutions such as banks are allowing customers to customize their login security controls and use simpler passwords if they opt for 2-Factor authentication.(14)
Two-factor authentication is also suggested as the best practice by CISA (Cybersecurity and Infrastructure Security Agency, USA). CISA puts single-factor login to a list of bad password practices.(15)
57.1% of the Respondents Say they Use 'Show Password' Option Only Sometimes
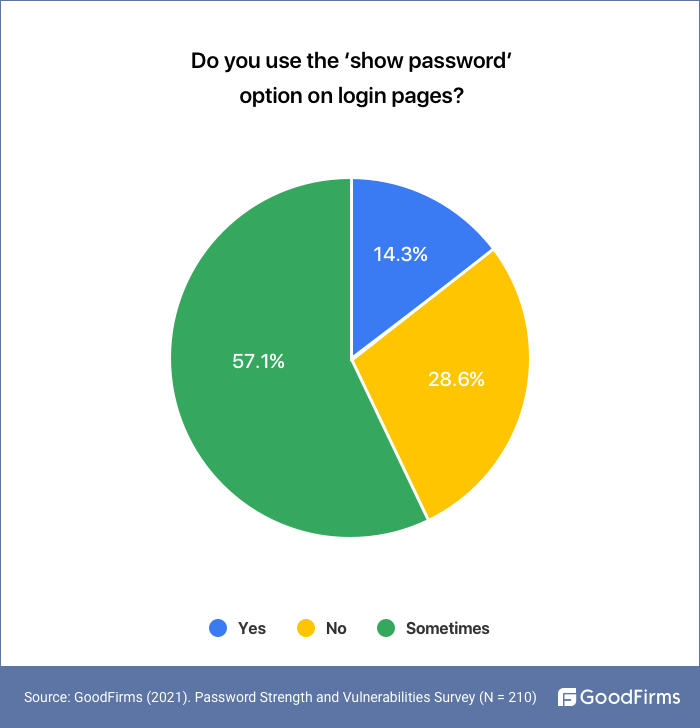
In the survey by GoodFirms, 14.3% of the users use the “show password” option, while 28.6% do not prefer to expose their secret code on-screen. A significant fraction (57.1%) sometimes use the 'show password' option while filling their private credentials online and have to use it.
Generally, while filling passwords online, typed letters of passwords are not shown and hidden with a process called Masking.(16) It means hiding the actual password and replacing it with characters like bullet points.
Users who need to enable the show password option do it for one of the below reasons:
- The initially entered password doesn’t match the requirement
- Keyboard input issues (Shift key not working, caps lock on, etc.)
- Forgetting what was typed and checking with show password option
- After one unsuccessful attempt at login, people generally enable the show password option to make sure that the next attempt is a success.
Best Password Practices in 2021(Experts’ Views)
As cybersecurity continues to be a major problem, GoodFirms queried top IT experts, CEOs of organizations, cybersecurity professionals for understanding the experts' take on password vulnerabilities, the threats due to a weak password, and the effectiveness of password management tools/techniques. Some of the best password practices for password protection and management suggested by experts in the field are discussed below:
#Word-Based Approach:
The word-based approach in passwords relates to using unique word combinations together that are obscure but easy to remember. Nate Tsang, the founder, and CEO of Wallstreetzen.com says that- "opting for a word-based approach is the best. Something like ScooterMonkeyApple is long and obscure enough to dissuade hackers, but evocative enough to be remembered by a user."
#Create Accounts With Trusted Companies Only
Mark Rapley, Director of Operations of KWIC Internet, suggests creating accounts only with companies that take user security seriously. "Multiple failed attempts to log in should be treated as an attempt to compromise the account, which should then lock access to the account until additional verification steps are taken to reset the password. Any password can be guessed if the hacker has infinite attempts, so limiting the number of attempts is crucial."
#Use Secure VPN Sessions:
Make sure you have a VPN (a virtual private network) that is safe and secure. You need to make sure that passwords used on VPNs are not compromised due to insufficient VPN protocols and poor threat detection systems. Ensure that VPN’s firmware is updated and the router is using all safety measures before using passwords on VPNs.
#Keep Your Password Policy a Secret
Given that people use their devices to do almost everything and anything, right from banking to personal transactions, the loss of a password will give the hacker access to every confidential information of a person. There is no denying that it is hard to come back from that loss. Bragging about your password policy or password techniques can jeopardize your password management efforts. Experts advise against revealing your or your organization's password mechanism to anyone.
#Businesses Can Hire Ethical Hackers to Crack Their Passwords:
Businesses can hire ethical hackers or “white hats” who are security experts trained to help find and fix the vulnerabilities, leakages, and loopholes in their password policies. Businesses can detect flaws if the hacker is able to break into the system. Ethical hackers use techniques such as social engineering, session hijacking, footprinting, enumeration, reconnaissance, and many more to gain access to the system and credentials to verify the strength of your password policies and network. Ethical hackers conduct a vulnerability assessment of your password methods and provide you with a detailed report about their strengths.
#'Salt and Hash' Passwords
It is one of the preferred ways to secure user data. In the 'Salt and Halt' method, some unique and random characters add up to make an arbitrary combination by salting. Thereby, the obtained muddle goes through scrambling or hashing based on a set algorithm.
#Multi-Factor Authentication (MFA)
The multi-factor authentication employed by MFA serves as an extra edge in protecting user data. It means, even if intruders get to decrypt the user password, they may not access the data. The authentication levels include 'something you know,' 'something you have,' and 'something you are.' It includes multiple filters guarding the data hidden behind the user password. Microsoft says MFA can block over 99.9 percent of account compromise attacks.(17)
#Avoid Dictionary Terms
Using meaningful words from the dictionary is the most basic pattern a user can opt for as a password. It can easily be hacked by intruders using specific pattern guessing tools.
#System Lockout Policy
When someone tries to access the protected data or information from the user's system and fails to decrypt the code multiple times, this feature locks the system automatically.(18) It not only covers the private data but everything available in the system.
#Create Password Building Rules:
Rather than using common words as it is, users can abbreviate them, misspell them, or join words to create passwords that are difficult to crack. For example, Orange can be written as Or, or Oragne, or users can combine orange+textbook+building to create Ortextbuild or Orbookding. To further strengthen the password users can add numerical and special characters and randomly capitalize the whole thing. For instance, OrbooKdiNg235$ will be a very strong password.
#Passwords Generated by Systems:
"Moore's law explains why a relatively weak password will not be sufficient for long-term use: Computers can uncover passwords quicker via brute force with time. A genuinely strong password, as defined by ANSSI, would consist of a sequence of 16 characters selected from a pool of 200 characters. This would result in a 123-bit gap, making the password extremely impractical to remember.” says Isla Sibanda, a Cybersecurity Specialist specializing in Ethical hacking. However, such passwords can be deployed using password managers or if the systems generate them automatically.
#No Anagrams or Palindrome
Using anagrams or palindromes of previously used passwords is a poor password policy. If a previously used password gets hacked, the close variations are tried by the hackers, such as anagrams. Avoid using anagrams.
#Unique Passwords for Multiple Sites
One of the most common reasons for people being unable to manage passwords is difficulty in remembering multiple passwords. However, according to research,(19) it is highly advisable to have a unique password for different login platforms considering the safety of user data.
#Sharing is Not Caring When it Comes to Passwords
Other issues arise when staff share passwords and access credentials with coworkers. It is essential for employees to understand that tight access controls are a cornerstone of any organization's security strategy. Coworkers and web applications, including instant messengers and email, can be hacked, so it is important no passwords are shared among systems or employees", says Mieng Lim, VP of Product Management at Digital Defense.
#Don’t Reuse or Recycle Passwords
Sometimes an old password that was used previously for an online account that is no longer in use is assigned to a new site login. However, it can be dangerous if the credentials stored in the old account get stolen. Hackers may use the password to try to login into your other currently working accounts. “Reusing or recycling passwords across different sites and systems just makes life easier for hackers," adds Lim.
#Complex Passwords For RDP Logins:
Most experts suggest using long and complex passwords for RDP (Remote Desktop Protocol) logins. RDP is a popular protocol developed by Microsoft for remote access to Windows-based systems. RDP allows users to control systems remotely. James Wilson, a Digital Privacy and Security Expert at My Data Removal, suggests creating long and complex passwords for RDPs using password creation tools if required.
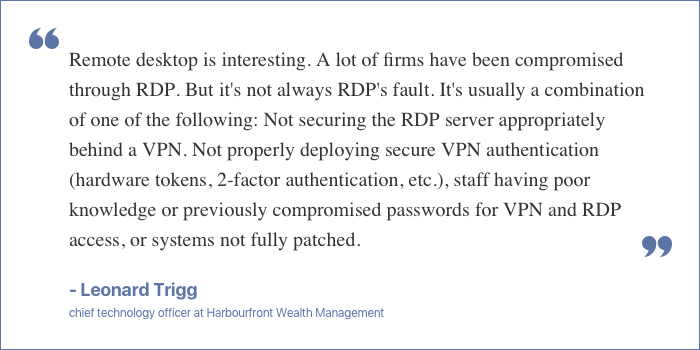
How to Strengthen RDP (Remote Desktop Protocol) Access and Protect its password credentials?
Remote desktop Protocol is the technique to connect with remotely situated desktop computers from a server computer. Remote desktop users can access their workstations, open and edit files, and use business applications as if they were physically sitting at their desktop computer. Employees can use, access, edit files situated on their work computers from another device when they are traveling or working from home.
While working remotely, employees need to connect to RDPs by using passwords and login credentials. However, it is critical to keep the password credentials safe to protect remote desktops from unauthorized use. Password stealing attempts are not always for money; sometimes, the purpose is stealing information, spying, sabotage, rivalry, revenge, etc. Therefore, strengthening RDPs is critical for employees and organizations. Experts queried by GoodFirms suggest the following ways to strengthen RDPs:
- Use Two-Factor Authentication for login
- Keep the software updated to ensure that bugs and patch loopholes are not exploited by hackers.
- Use firewalls
- Set up an access policy and an account lockout policy
- Use VPNs to protect the RDP network
The Future of Password Security:
Will passwordless be the future login solution?
Will biometrics and facial recognition completely take over passwords?. Will we have a safer login without passwords? Will the vulnerabilities be a thing of the past? Will password management without adding friction to the user experience ever take place?
Today password-based authentication dominates all other mechanisms of verification in the online realm. However, access management with passwordless identity verification has been gaining traction recently. Voice commands, facial recognition, fingerprints, biometrics, etc., are replacing the need for remembering, managing and protecting passwords. In 2019, the World Wide Web Consortium (W3C) approved the protocol for Web Authentication API (WebAuthn) that lets login to websites without passwords.(20) Similarly, FIDO presents a free and open-source method of authentication without passwords.(21)
The world is heading towards a passwordless era. The post-password world might look like as Mckinsey research says- “It would probably combine biometric authentication or authentication based on devices (such as phones, which use biometrics) with behavioral analytics that can determine, probabilistically, if users are legitimate.” By 2022, Gartner predicts that 60% of large and global enterprises, and 90% of midsize enterprises, will implement passwordless methods in more than 50% of use cases — up from 5% in 2018.(22) However, initial financial investment, time to move systems to the passwordless regime, and regulatory hurdles are a few challenges that passwordless login models have to face before replacing passwords as the preferred mode of authentication.
Key Findings
- 62.9% of people change their passwords only when prompted
- 45.7% of people reuse a password for multiple sites/applications
- 52.9% of people have shared their password with colleagues, friends, family members
- 67.1% of the people support that managing passwords for multiple accounts is not a waste of time.
- 35.7% of the people still jot down their passwords on paper, sticky notes, or use planners.
- 30% of the users have experienced security breaches due to weak passwords.
- 88.6% of users queried in the GoodFirms' survey use two-factor authentication
- 57.1% of the respondents use the 'show password' option while filling credentials over online login pages, sometimes
- Making passwords stronger is the first step to prevent unauthorized access to online accounts
- Password managers are a great solution for managing passwords, especially for people with less cybersecurity knowledge.
Some best password protection and management practices for unhackable passwords are:
- Using complex and long passwords for RDP logins
- Creating accounts with trusted companies only
- Using 2-Factor authentication wherever applicable
- Using secure VPNs
- Setting up a password generation policy and keeping it secret
- Not using dictionary terms, common phrases, personal info in passwords
- Deploy a password management software tool for managing passwords effectively.
Conclusion
From single sign-on to multi-factor authentication, password practices have evolved with time. As password authentication technology gets stronger and more foolproof, it is also the responsibility of users to protect their passwords from cyber attackers by following the best practices. This research concludes that users should adopt the best practices to protect their online credentials and safeguard their passwords. Users can also utilize services of tools such as password managers to create a robust security cover and password management system for all their online accounts.
GoodFirms’research team has taken extreme measures to keep the survey data immaculate, the process objective, and insights empirical to benefit businesses that need more information to cater to their customers in a better way. For queries related to the research, reach out to [email protected]
We sincerely thank our Research Partners who participated in the survey.
References
- https://www.ntsc.org/assets/pdfs/cyber-security-report-2020.pdf
- https://users.ece.cmu.edu/~lbauer/papers/2020/breaches-conpro2020.pdf
- https://www.forbes.com/sites/forbestechcouncil/2021/01/04/make-better-password-habits-one-of-your-new-years-resolutions/?sh=70002e4a7173
- https://www.nacdl.org/Landing/ComputerFraudandAbuseAct
- https://www.cnbc.com/2019/01/30/netflix-price-hike-may-spur-growth-in-illegal-password-sharing.html
- https://www.businessinsider.in/tech/a-password-for-the-hawaii-emergency-agency-was-hiding-in-a-public-photo-written-on-a-post-it-note/articleshow/62531465.cms
- https://crypto.stanford.edu/~dabo/pubs/papers/pwdmgrBrowser.pdf
- https://www.usenix.org/conference/usenixsecurity20/presentation/oesch
- https://www.mckinsey.com/business-functions/risk-and-resilience/our-insights/cybersecurity-in-a-digital-era
- https://www.identityforce.com/blog/2021-data-breaches
- http://www.nytimes.com/2010/01/21/technology/21password.html
- https://www.usenix.org/conference/soups2019/presentation/reese
- https://ieeexplore.ieee.org/abstract/document/8256716
- https://www.mckinsey.com/business-functions/risk-and-resilience/our-insights/cybersecurity-in-a-digital-era
- https://us-cert.cisa.gov/ncas/current-activity/2021/08/30/cisa-adds-single-factor-authentication-list-bad-practices
- https://dl.acm.org/doi/abs/10.1145/3411763.3451667
- https://www.microsoft.com/security/blog/2019/08/20/one-simple-action-you-can-take-to-prevent-99-9-percent-of-account-attacks/
- https://link.springer.com/chapter/10.1007/978-3-030-37231-6_2
- https://research.csc.ncsu.edu/efg/ethics/papers/passwords.pdf
- https://www.w3.org/TR/webauthn-2/
- https://fidoalliance.org/
- https://www.gartner.com/smarterwithgartner/embrace-a-passwordless-approach-to-improve-security